· Exploitation · 8 min read
NAT Slipstreaming
NAT Slipstreaming Exploit: A Unique Threat to Network Security

Overview
NAT Slipstreaming, This sophisticated attack technique allows malicious actors to remotely access any TCP/UDP service hosted on a victim machine, effectively bypassing the NAT or firewall security controls given that the victim visits a website.
What is NAT Slipstreaming?
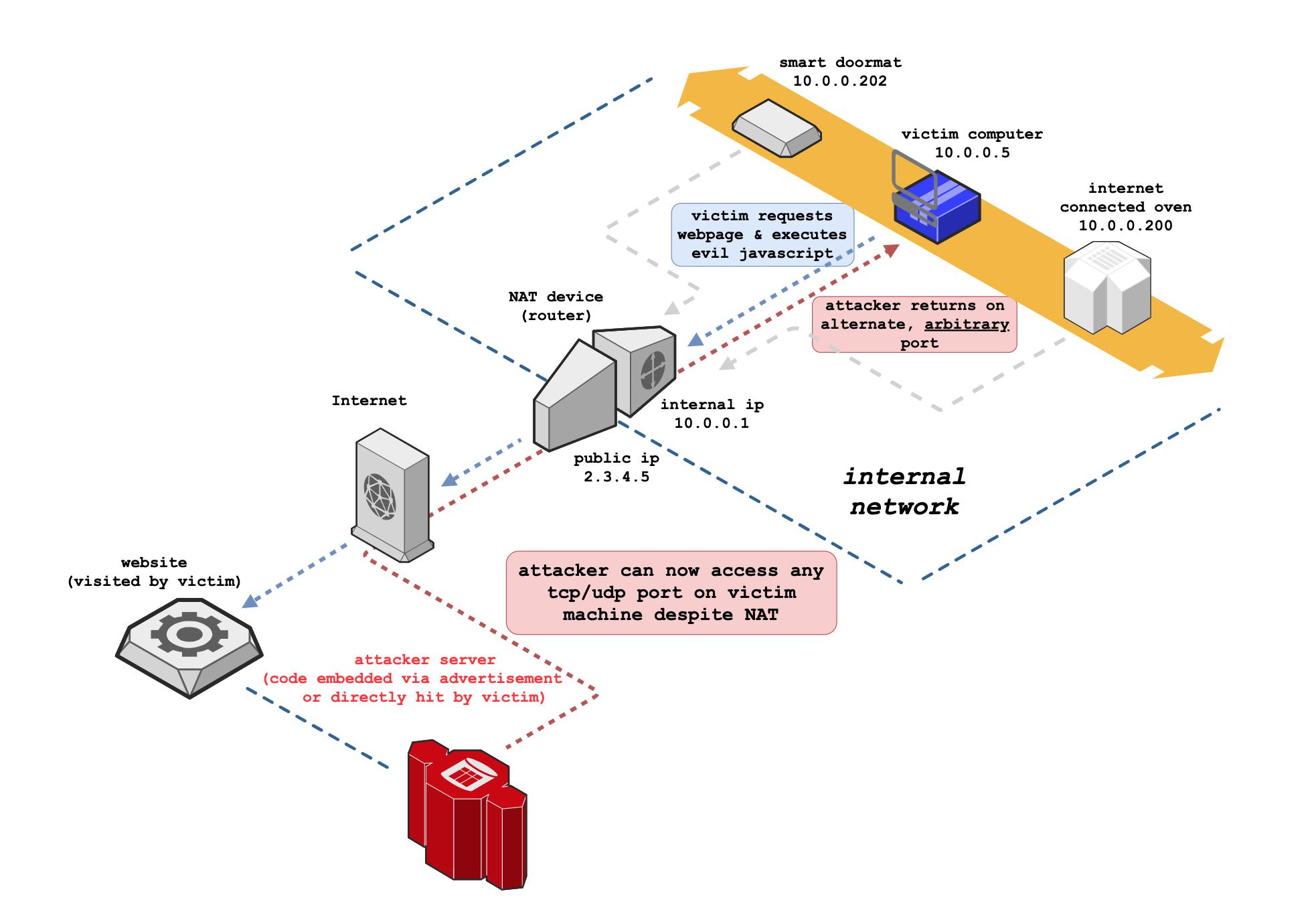
Network Address Translation (NAT) is a mechanism that remaps an IP address space for traffic passing through a networking device. While NAT has been instrumental in conserving IPv4 address space and offering some security benefits, NAT Slipstreaming exposes vulnerabilities that render these protections ineffective.
Developed by security researcher Samy Kamkar, the NAT Slipstreaming attack leverages a combination of techniques to exploit the Application Level Gateway (ALG) functionalities in NAT/firewall systems. ALG is essential for protocols requiring multiple ports, such as VoIP protocols like SIP and H323, and FTP. The attack exploits the user’s browser in conjunction with ALG connection tracking mechanisms, utilizing JavaScript to manipulate TCP/UDP packets’ data portions.
How NAT Slipstreaming Works
The attack chain begins with the victim accessing a malicious website, which runs JavaScript code to control the data portion of TCP/UDP packets. This crafted packet injection technique works across all modern browsers (nowadays most modern web browsers, including Chrome and Firefox, block port 5060 by default because of it) and exploits various protocols and features to create a complex interaction that bypasses NAT/firewall restrictions.
NAT Slipstreaming exploit involves:
- Internal IP Extraction: Using timing attacks or WebRTC.
- Remote MTU and IP Fragmentation Discovery: Automated techniques to discover the Maximum Transmission Unit (MTU) and fragment IP packets.
- TCP Packet Size Manipulation: Adjusting packet sizes to align payloads appropriately.
- TURN Authentication Misuse: Exploiting TURN servers for WebRTC connections.
- Protocol Confusion: Misleading the NAT/firewall into interpreting non-HTTP packets as legitimate traffic that requires opening ports.
The Evolution: NAT Slipstreaming v2.0
A new variant of the attack, discovered by researchers Ben Seri and Gregory Vishnipolsky from Armis, in collaboration with Samy Kamkar, further extends the exploit’s capabilities. This variant enables attackers to reach any device within the internal network, not just the initial victim machine. The impact can range from minor nuisances to severe ransomware attacks.
Technical Breakdown and Mitigation
The original attack relied on a victim clicking a malicious link, which tricked the NAT into opening an incoming path from the internet to the victim’s device. The new variant exploits the H.323 ALG to create pinholes for any internal IP, accessible via WebRTC TURN connections. This bypasses browser-imposed port restrictions, allowing access to ALGs like FTP and IRC.
Notably, this variant v2.0 affects enterprise-grade NATs/firewalls from vendors like Fortinet, Cisco, and HPE. The collaboration led to a coordinated security disclosure with major browser vendors, resulting in patches from Google, Apple, Mozilla, and Microsoft.
To mitigate these risks, browser vendors have:
- Added TCP/UDP ports of known ALGs to the restricted ports list.
- Enforced these restrictions on WebRTC connections.
- Consider using or enhancing network monitoring tools, especially for specific vendors that use the IE browser solely.
The Broader Implications
NAT Slipstreaming reveals a fundamental issue with how NATs are implemented. While browser patches offer a short-term fix, a long-term solution requires a reevaluation of NAT design and a shift towards IPv6 adoption. The internal security teams must remain vigilant, as the interplay between modern browsers and legacy network appliances continues to present. Check out our Security Monitoring service to see what we’re offering!
