· Customer Success · 8 min read
Mobile Application Security - Pentesting Success Story
How Advanced Security Identified and Resolved a Critical Vulnerability in Spell Valley's In-Game Economy

Overview
In the competitive mobile gaming world, ensuring a secure in-game economy is crucial. Bad Bishop, the creator of Spell Valley, faced a security issue that threatened their game’s balance. With the help of Advanced Security’s expert pen-testing services, they identified and resolved the vulnerability, safeguarding the game’s economy and player trust.
The Challenge: A anomaly in Spell Valley’s Economy
The issue at hand pertained to a critical anomaly within Spell Valley’s economic framework. Bad Bishop, discerning a possible vulnerability, approached Advanced Security under the premise that it might enable players to acquire Gems (integral virtual currency) without expenditure.
Identifying the Vulnerability
Using advanced tools like tcpdump and Wireshark, our pen-testing team discovered that the Spell Valley application was proxy unaware, attempting to connect to its API endpoints with random ports. (The screenshot of Wireshark is only for illustrative purposes, with real information withheld to ensure the confidentiality and protection of our clients.)
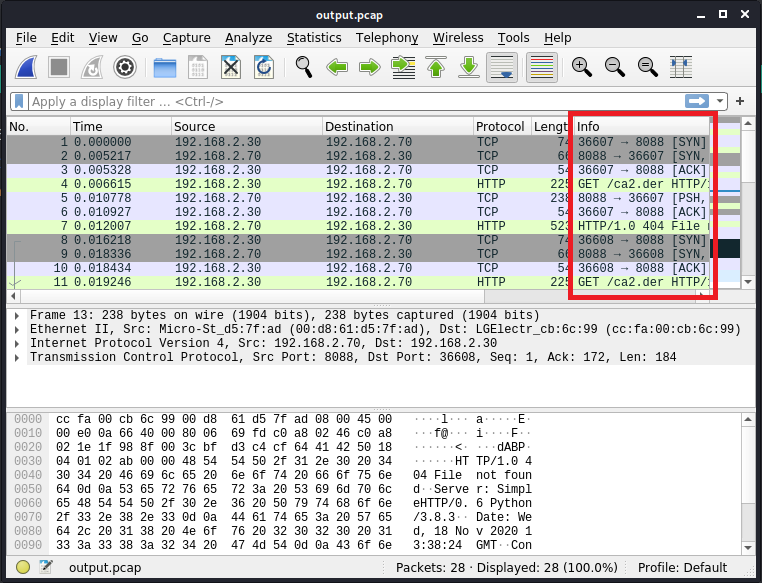
This allowed us to intercept and analyze the traffic using Burp Suite by setting up appropriate iptables rules and using adb reverse to map a port on the device to the Burp instance.
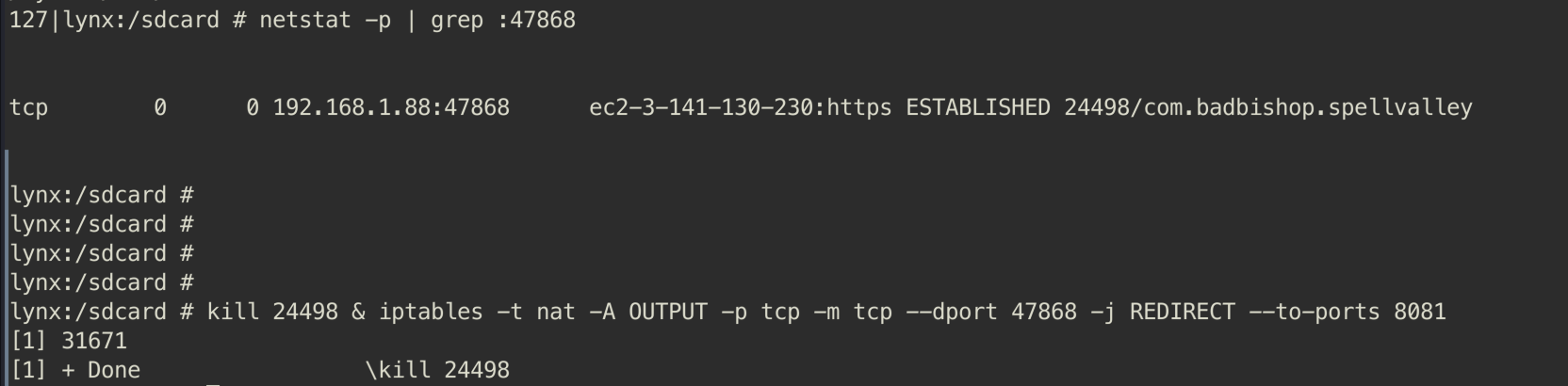
Once the setup was complete, we used Objection with Frida to bypass any potential SSL pinning issues and began observing the traffic through Burp Suite.
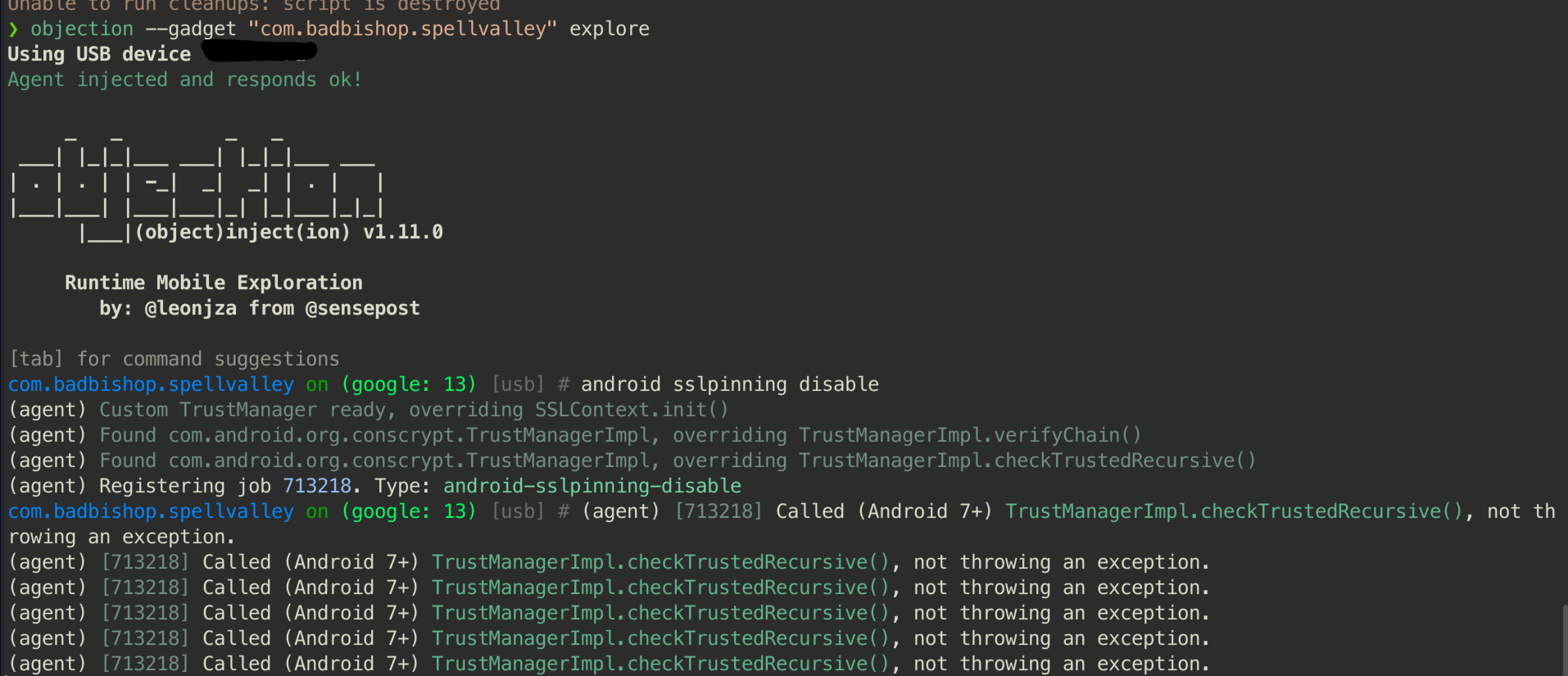
We noticed that we could see all the ongoing endpoints and their parameters, which led us to run Burp Intruder to brute force chest IDs.
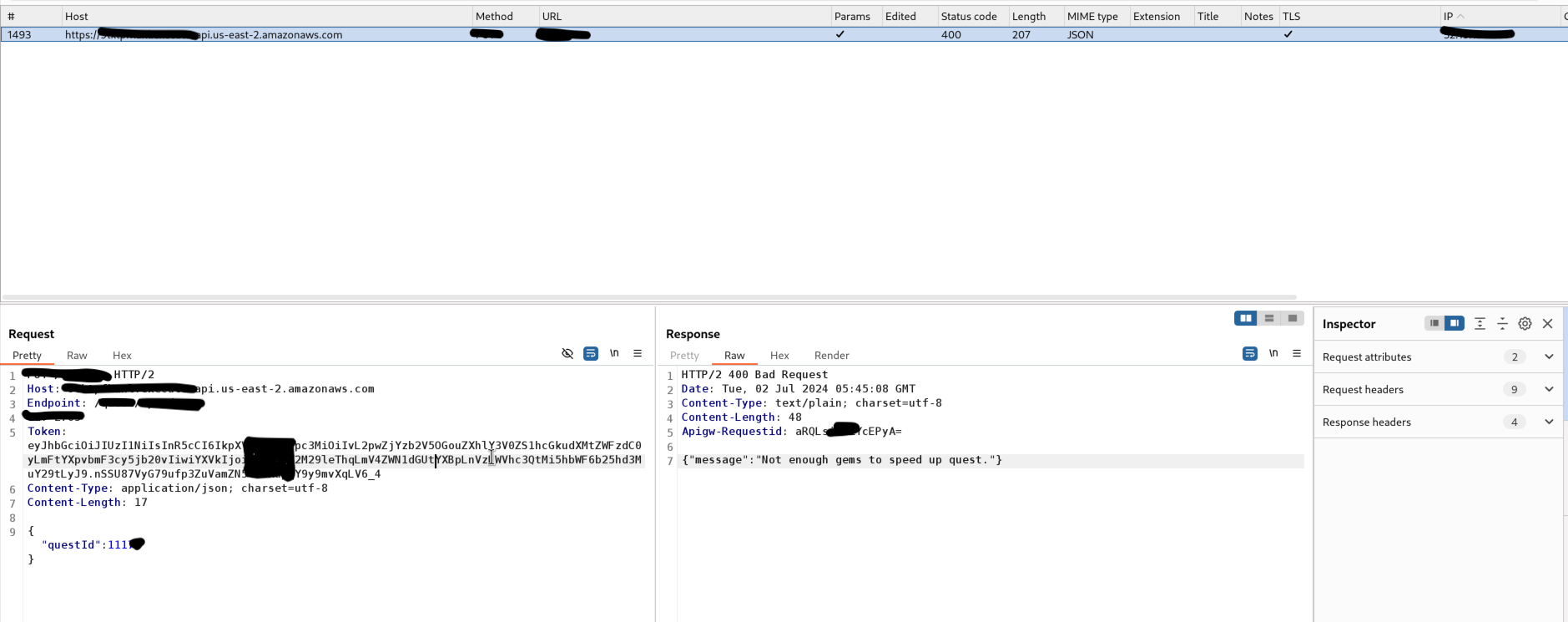
Exploiting the Bug
After successfully brute-forcing chest IDs, our team was able to repeatedly claim rewards, accumulating up to 20K Gems in a short period. Further investigation revealed that by using a specific endpoint, we get Gems for free.


The Solution: Swift and Effective Bug Fix
We immediately reported our findings to the Bad Bishop development team. Through collaborative discussions, we identified the root cause of the vulnerability. The bug was due to a flaw in the server’s logic leading to negative gem costs and the ability to repeatedly exploit the system.
Collaborative Debugging and Fix Implementation
Bad Bishop’s lead developer, worked closely with our team to debug and verify the issue. Using custom scripts and database checks, we confirmed the exact conditions under which the exploit occurred. The dev team then implemented a fix to ensure that quests in the claimed state could no longer be mistakenly processed as redeemable.
The Outcome: A Secure and Fair Gaming Experience
Thanks to the thorough pen-testing and quick response by the Advance Security and Bad Bishop team, the vulnerability was promptly addressed before any significant impact could materialize. Check out our Pentesting service to see what we’re offering! Check out our listing as a top IT services company in the New Zealand IT services agency
